Premium Photo | System developer writing lines of codes in order to build a anomaly analyser for database. cyber security agency network developer doing ethical hacking to retrieve encrypted stolen data. close

New Irish website aims to stop people from unknowingly buying stolen goods by creating database of robbed property | The Irish Sun

China censors news on hacker selling personal info of 1 billion citizens from stolen police database

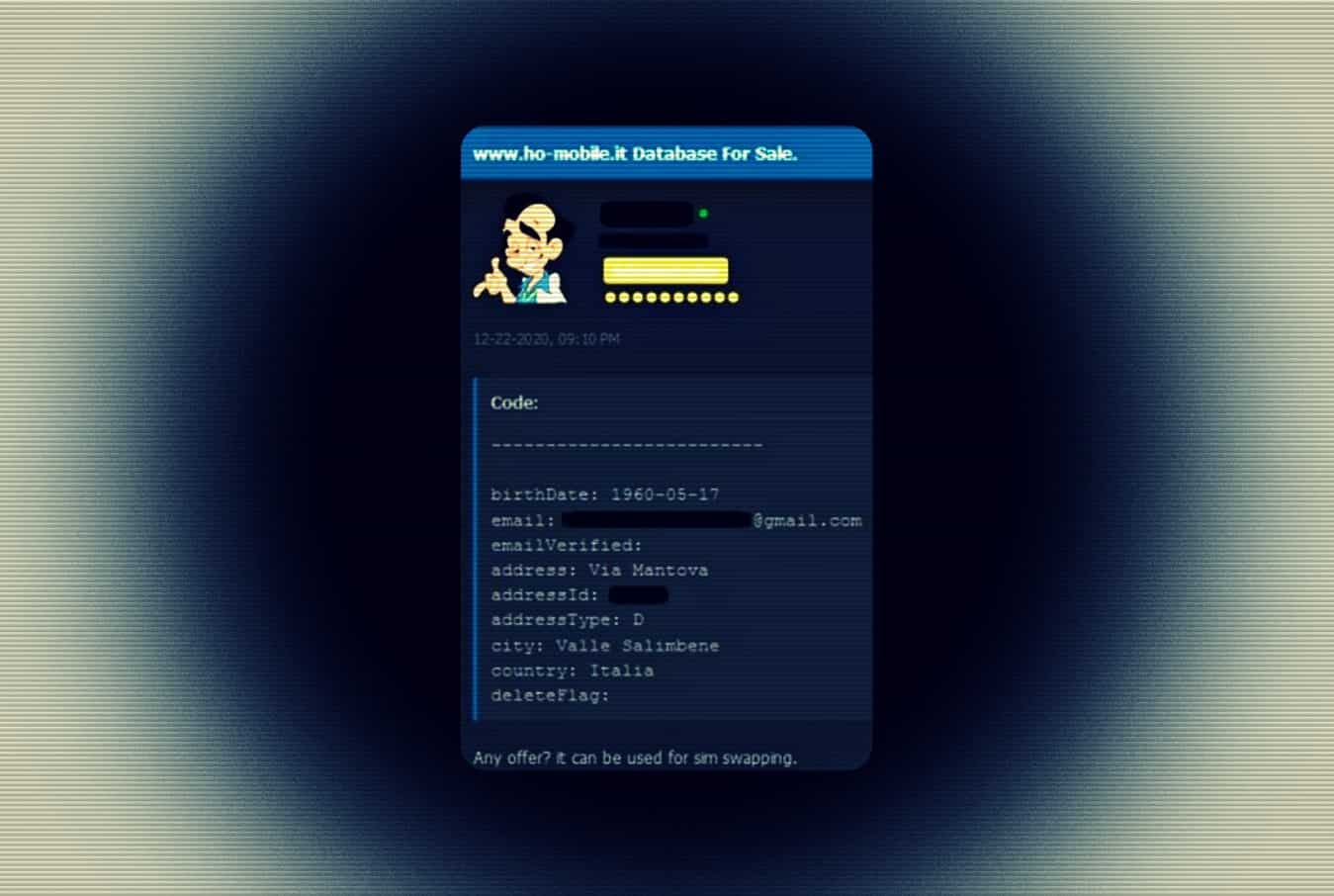
Misconfigured database operated by hackers found exposing almost 5GB of stolen credentials | Cyware Alerts - Hacker News

Free Photo | African american software developer pointing out cloud database processing algorithm error. cybernetics engineers deciphering stolen corrupted and … | Software development, African american, Free photos

Leaked Personal Data of 1 Billion Chinese Citizens on Sale for 10 Bitcoins — Hacker Claims Stolen From Shanghai Police – Security Bitcoin News
African american software developer pointing out cloud database processing algorithm error. Cybernetics engineers talking about deciphering stolen corrupted and ecrypted important company files Stock Photo - Alamy














:max_bytes(150000):strip_icc()/identitytheft.asp-final-7eb6d3e2b3434994bcb40226957e3b3c.jpg)