Protect your digital systems from brute force attacks. | Pyramid Cyber Security & Forensic posted on the topic | LinkedIn
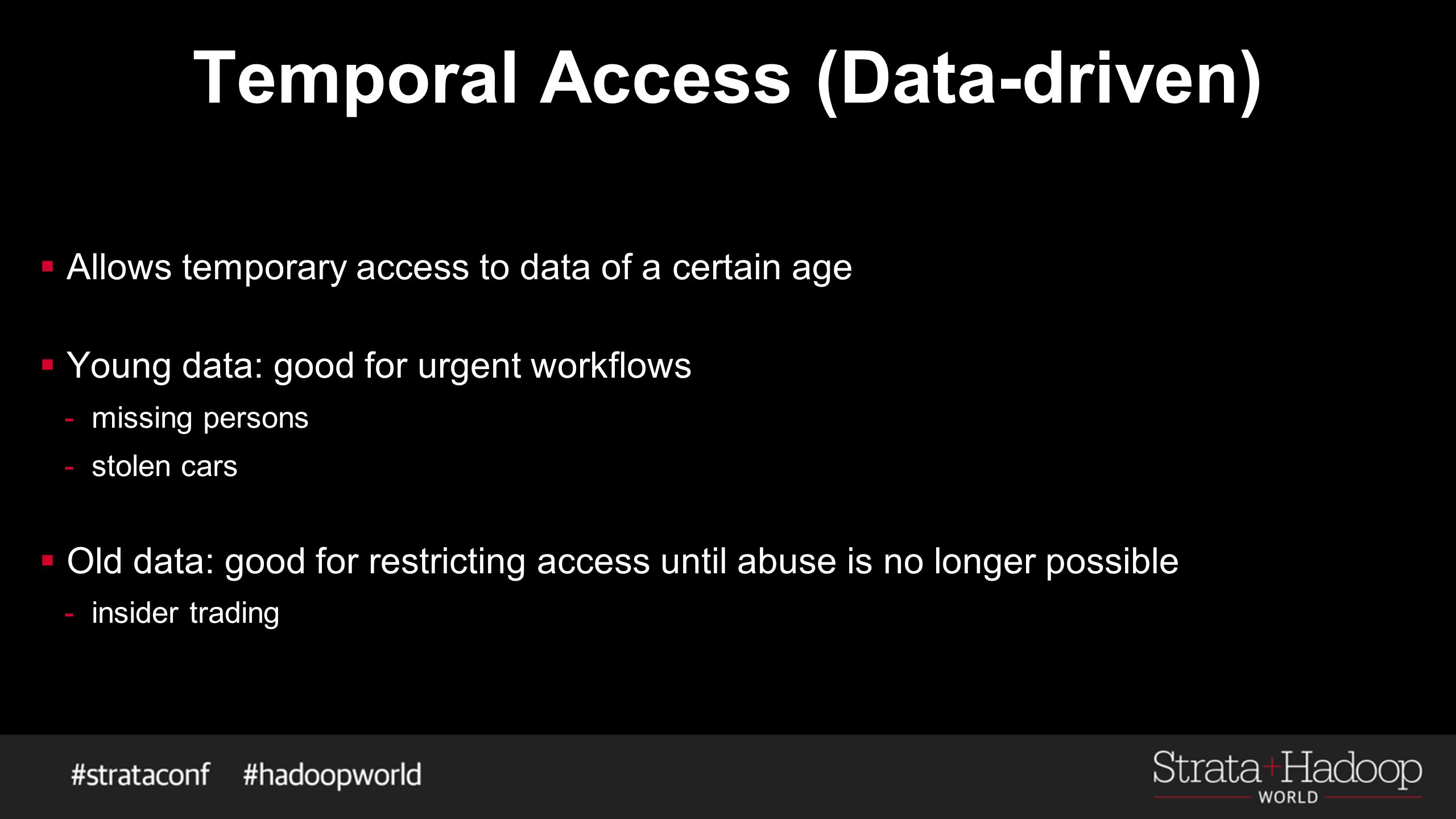
Building Privacy-Protected Data Systems Courtney Bowman Ari Gesher John Grant (of Palantir Technologies) - ppt download

'I didn't give permission': Do AI's backers care about data law breaches? | Artificial intelligence (AI) | The Guardian


![Remove "Your ICloud Is Being Hacked!" Pop-ups [Virus Removal] - MalwareTips Blog Remove "Your ICloud Is Being Hacked!" Pop-ups [Virus Removal] - MalwareTips Blog](https://malwaretips.com/blogs/wp-content/uploads/2023/04/Your-iCloud-Is-Being-Hacked.jpg)